Driving meaningful connections and enhancing customer engagement in life sciences
Learn about the most critical aspects of customer engagement and how to build and implement a reliable strategy for long-term success.

Explore the importance of cyber resilience and compliance to standards like HIPAA, CCPA, ISO 27001, SOC2, and GDPR in order to protect health information and avoid hefty fines.
The average cybersecurity breach in the pharmaceutical industry is estimated at costing $5.06 million. Yet, to help companies mitigate potential breaches, data security standards are designed to lower the chances of sensitive data being stolen.
This article is dedicated to those standards. A major point is to show how noncompliance with HIPAA, CCPA, ISO 270001, SOC2, and GDPR make companies’ cybersecurity vulnerable to threats. In addition, it is crucial to illustrate the simple steps toward compliance and argue the benefits of such an approach.
Why is cybersecurity important in pharma? There are two particular answers to this question. First, it is worth noting that the global cybersecurity market is booming, which means more companies work with more clients and their data. With more companies adopting digitization, there is a growing demand for effective cybersecurity measures. Statista forecasts the global cybersecurity market will reach $345.4 billion by 2026 compared to $217.9 billion in 2021 (see Fig.1).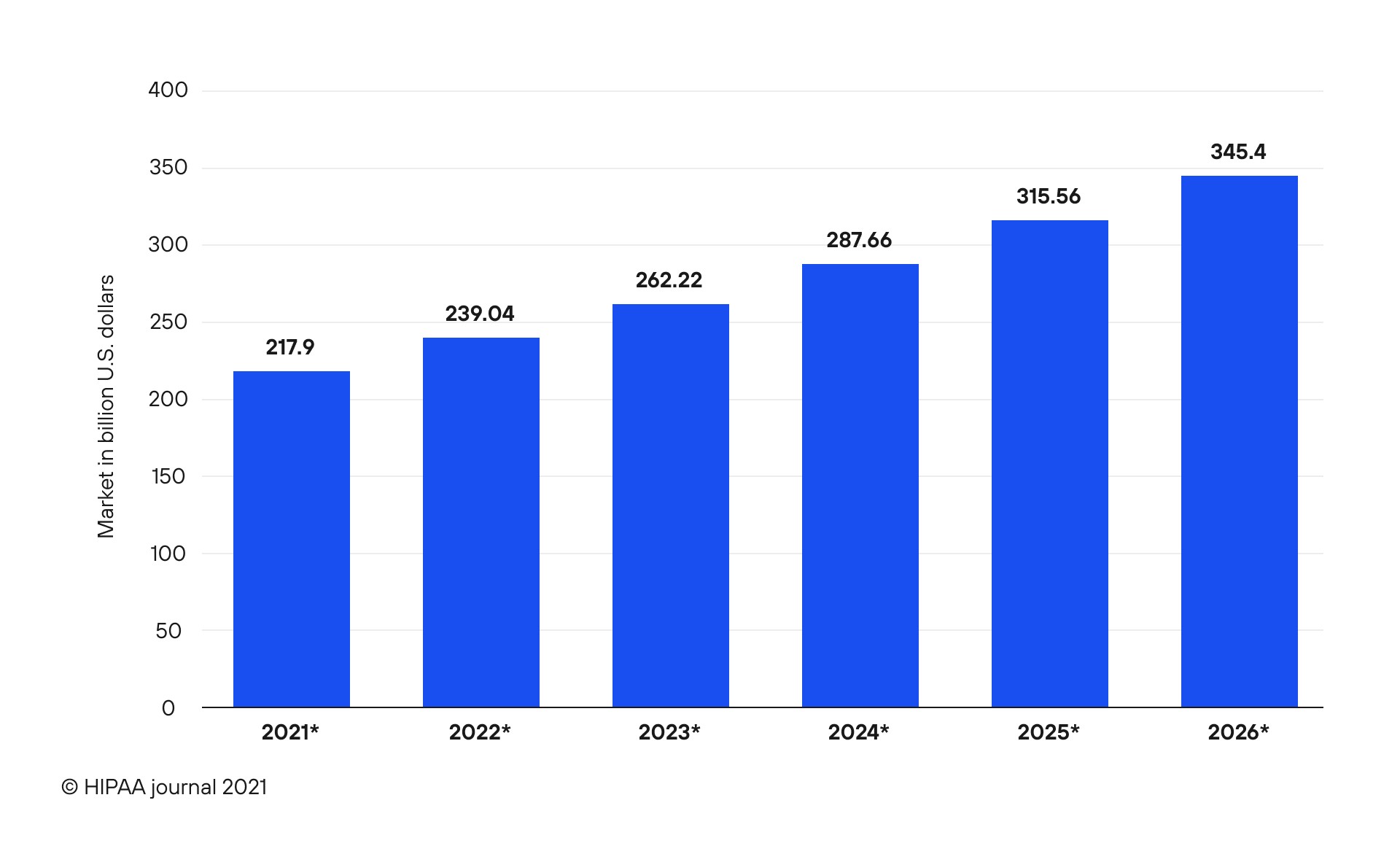 Figure 1. Size of the global cybersecurity market worldwide
Figure 1. Size of the global cybersecurity market worldwide
Second, the importance of data security in pharma is measured by the number of data breaches that happened in the past and the degree of damage inflicted by them. In a nutshell, more and more costly security breaches are happening every year. To illustrate the harm that can be inflicted by security breaches, here are several key examples from the pharmaceutical industry.
A recent report from cybersecurity agency Black Kite suggests that about 89 percent of pharma companies are at risk of experiencing a phishing attack. To illustrate, in September 2014, the pharma industry became a victim of a targeted malware attack resulting in intellectual property theft. More specifically, the so-called Dragonfly malware infected thousands of business computers while collecting pharma control systems information across the U.S. and Europe. As a result of the attack various pharma companies were forced to postpone ongoing drug discovery processes.
A NotPetya attack took place in 2017. It was immediately coined as one of the most damaging cyber attacks in history. While initially directed by Russia against Ukraine, the pharmaceutical giant Merch was hit as a result of the attack. The malware took down around 30,000 computers across the company’s different departments. An estimation suggested that the cost of the damages from the attack was about $1.3 billion. In addition, the malware disrupted the production of an important HPV vaccine produced by Merck.
The case of Bayer and Roche emphasizes the importance of creating potent statewide health care security. In the so-called Winnti attacks, an alleged China state-backed hacker group targeted Bayer. While the company managed to mitigate the attack and no data theft occurred, the case raises an important question concerning industrial espionage.
One of the most recent cases targeting pharma cybersecurity is linked with Pfizer and AstraZeneca. In December 2020, the European Medicines Agency (EMA) indicated the breach of privacy and security in pharma-associated documents corresponding to the Pfizer vaccine. At the same time, hackers from North Korea initiated a spear-phishing campaign against AstraZeneca. At this point, along with sensitive information being stolen, both companies suffered about $5 million in losses.
Statista illustrates that in 2021 the average cost of a data breach revolved around $4.24 million, an increase from $3.84 million experienced in previous years (See Fig.2).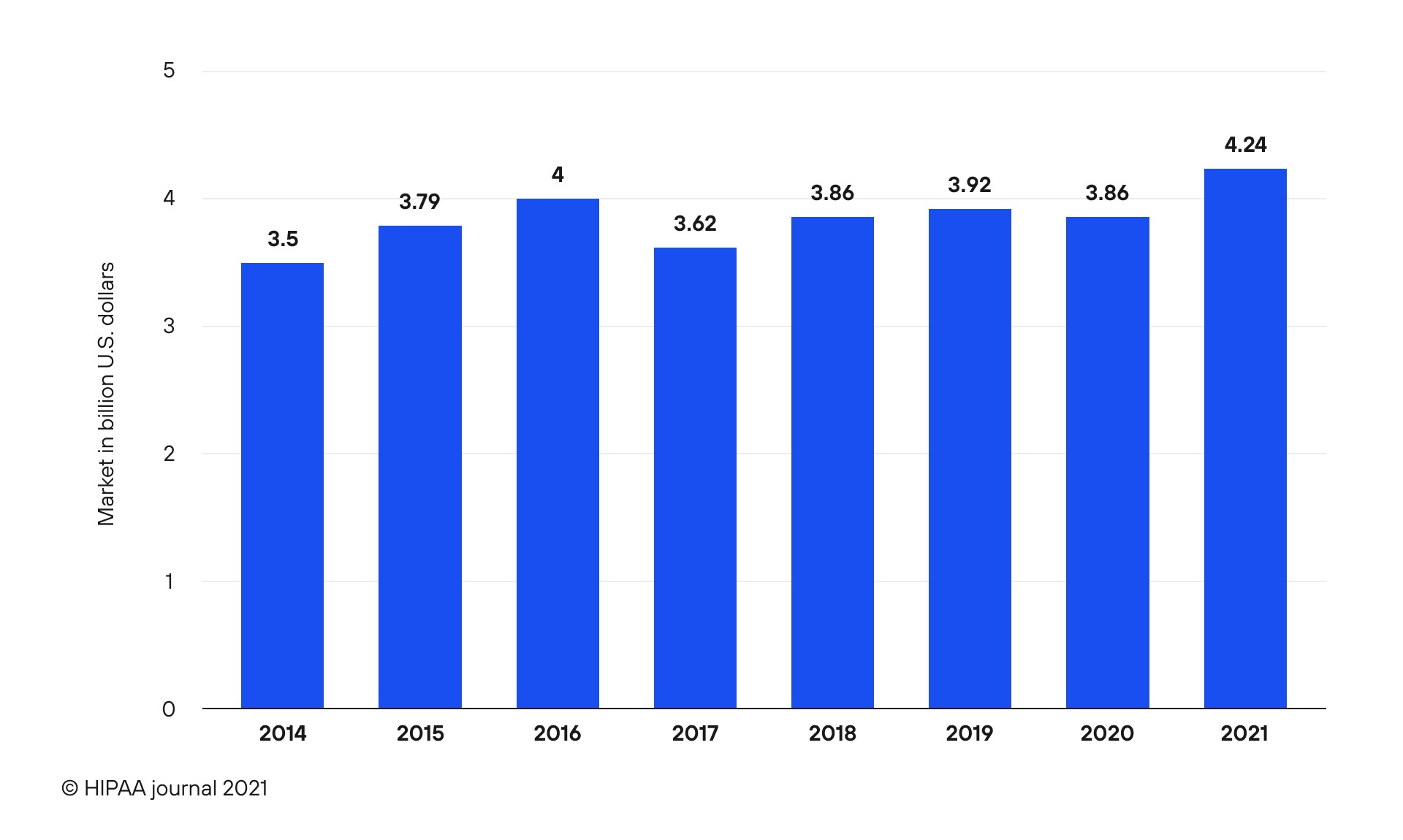 Figure 2. The average cost of data breaches worldwide.
Figure 2. The average cost of data breaches worldwide.
The data breaches in recent years show that the pharmaceutical industry is a legitimate target for malicious attacks. Through this perspective, cybersecurity in pharma gains an even greater significance. This is a time when pharma data security standards are coming to light.
What is privacy in healthcare and pharma? Privacy means ensuring a patient’s sensitive data is in good hands and protected from being disclosed without a person’s consent. Pharmaceutical companies follow particular guidelines and adhere to existing security standards to protect patient privacy. At this point, HIPAA is at the forefront of proper data security.
Known as the Health Insurance Portability and Accountability Act, HIPAA was signed in 1996. Generally, the law offers the following protections:
Regarding cybersecurity in healthcare, Title II of HIPAA offers specific guidelines for storing, processing, transferring, and accessing electronically protected health information (ePHI). At this point, noncompliance with HIPAA security rules often results in data breaches and hefty fines. An estimation shows fines ranging from $100,000 to $2.6 million (see Fig.3).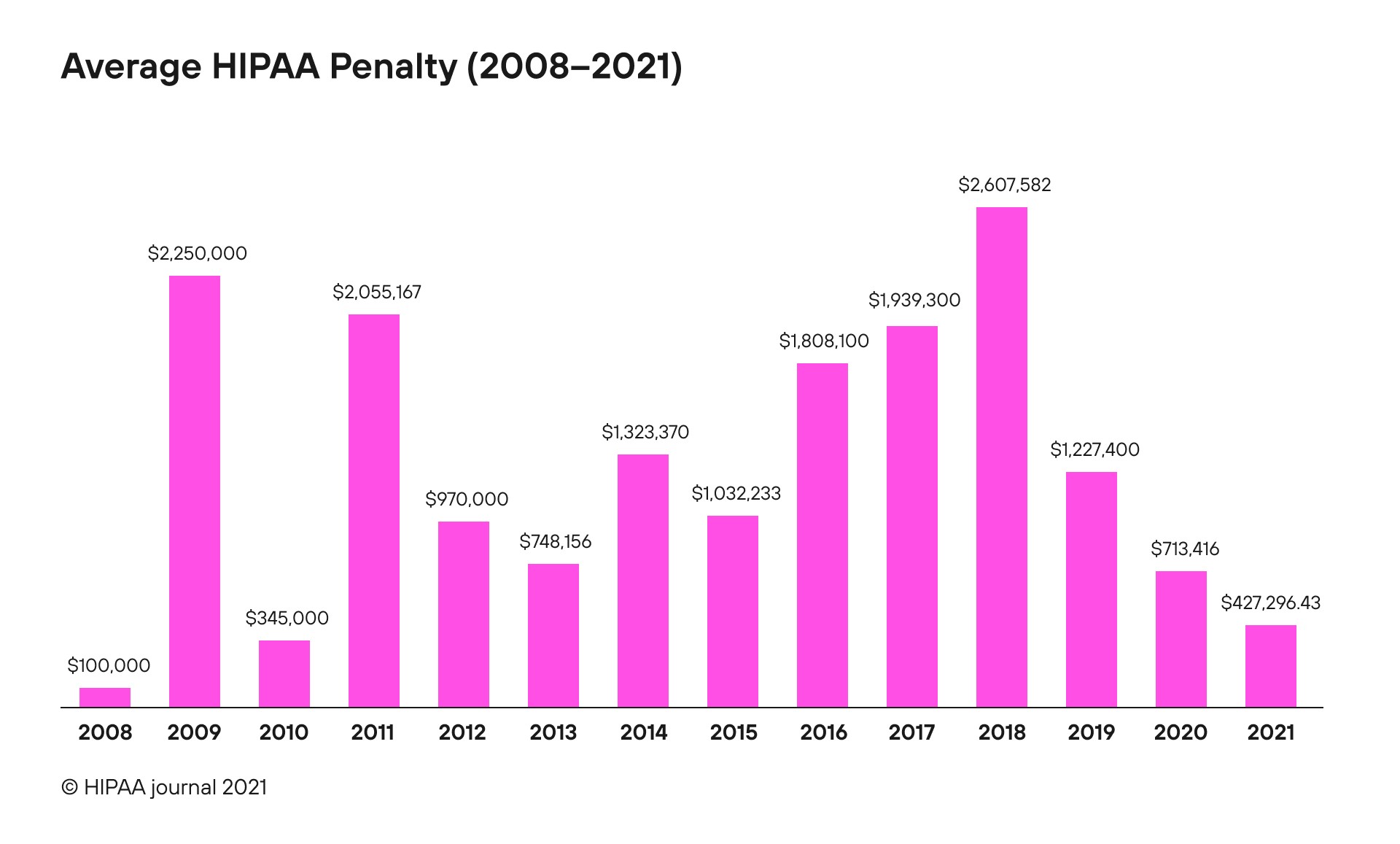 Figure 3. Average HIPAA penalty 2008-2021.
Figure 3. Average HIPAA penalty 2008-2021.
There is a dedicated HIPAA’s “Wall of Shame,” which is an online portal showing all the data breaches with information like the number of individuals impacted, type of breach, and the breach submission date.
Compliance with HIPAA security rules relies on several key principles:
HIPAA offers simple and effective protective measures to help pharma providers avoid damaging data breaches and hefty fines associated with noncompliance.
The California Consumer Privacy Act (CCPA) is an American version of the EU’s GDPR. Yet, instead of banning businesses from collecting consumers’ data, the standard focuses on the biggest tech corporations like Google, Amazon, and Facebook. Essentially, there are three given criteria determining whether CCPA applies to the business or not:
The standard’s important connotation is linked to the perception of a “consumer.” Following Section 17014 of Title 18 of the California Code of Regulations, CCPA does not apply to a consumer if they are not a California resident. In the context of pharma, the standard applies to clinical research and the security of medical databases.
Compliance with CCPA also requires considering the various HIPAA exemptions. One key exemption is applied to Protected Health Information (PHI). Such markers are collected and used by HIPAA as “Covered Entities” and “Business Associates.” In other words, pharma and life science companies offer healthcare services not covered by “Covered Entities” when processing patient health information.
Finally, in terms of the consequences of noncompliance, breaking CCPA standards often results in civil penalties ranging from $2,500 for a non-intentional violation to $7,500 for an intentional violation. For pharma companies operating in California, CCPA is worth considering, especially along with the HIPAA security rules.
Dealing with privacy and security in healthcare and pharma often results in numerous major challenges associated with data protection. For example, ISO 27001 is a standard that encourages a business to consider the process of data protection. More specifically, the controls in the standard offer suggestions on how such processes can be implemented and improved to become more feasible. Furthermore, ISO27001 encourages companies to implement sets of technical measures and controls to ensure data confidentiality, integrity, availability and safety.
ISO 27001 takes a holistic approach to cybersecurity in pharma. It entails aspects like risk assessments, risk treatment plans, inventory of assets, and key roles of users. There is a range of benefits compliance to ISO 27001 offers, including:
In the wake of recent events, there were three major cyber attacks in the Indian pharma industry. They took place for several months in 2020. As a result of the attacks, over 121 million medical records were compromised. The investigation showed a direct correlation between noncompliance to ISO 27001 and the companies’ insufficient security measures to repel the malicious cyber attacks.
To get ISO 27001 certification, a company needs to complete a compliance checklist:
Following the aspects mentioned above results in functional risk-based cybersecurity, meaning that the company is ready to mitigate any data breach or prevent it from happening in the first place. This results in protected health information and the ability to repel security threats effectively.
System and Organization Controls for Service Organizations 2 (SOC 2) is a framework that helps determine whether an organization’s practices are proven to be effective in protecting customer and client data. SOC 2 is mostly applied to companies that store data in the cloud, which is the case in the SaaS sector.
In the pharma industry, SOC 2 offers clear security protocols associated with the usage of patient data. For instance, if a company develops medical devices and in some manner maintains or transfers sensitive patient information, the SOC 2 standard provides reports illustrating how information security should be applied, especially when dealing with Personal Health Information (PHI).
Being SOC 2 compliant offers a range of benefits. Most notably, undergoing the audit illustrates that the company or provider has sufficient security to operate with patient health information. A SOC 2 certification boosts a company’s reputation as well. In addition, adherence to data security standards often translates into a competitive advantage. The highest levels of data security mean the highest levels of reliability.
Becoming SOC 2 compliant relies on the proper understanding of preparing SOC 2 reports. A starting point is to adhere to the Trust Service Principles: Security, Availability, Processing Integrity, Confidentiality, and Privacy. A SOC 2 report offers assessments on each of these principles. Here is more information on preparing SOC 2 reports, per each principle.
General Data Protection Regulation (GDPR) is the European data protection legislation enforced in May 2018. Under this principle, organizations operating with the personal information of any EU data subjects are obliged to demonstrate compliance or face penalties in the high millions. Essentially, to avoid hefty fines, companies operating with the personal data of Europeans need to show how they will protect it. This means illustrating how data from supplies, clinical trial subjects, and consumers are managed, transferred, and stored for pharmaceutical companies.
Usually, pharma companies store massive amounts of patient health information. Following the rules of GDPR, everything from patient databases to consumer communications records need to be protected from breaches. In addition, GDPR is especially important when dealing with medical research in the pharma industry. If using anonymous data is impossible, pharmaceutical companies engaging in medical research need to protect patient privacy through measures like:
Taking things further, in pharmacovigilance, there is an additional measure applied. Notably, GDPR requires businesses to report adverse reactions correlated with the principles of patient consent.
The crucial aspect is to consider the consequences of GDPR noncompliance. A so-called “GDPR Noncompliance Tracker” offers a great deal of information on all companies who have received hefty fines because of their inability to apply such significant security standards. Several examples are worth noting to show the extent of recent GDPR-related penalties. In 2021 Amazon was issued a staggering $877 million fine. Another instance is WhatsApp, the platform paid a $255 million fine. Finally, Google Ireland, failing to adhere to GDPR rules, was fined $102 million.
With the massive fines, millions of people were affected as well. A HIPAA report indicates that 2015 peaked in the number of individuals affected by data breaches. In terms of sheer numbers, more than 113 million people were affected by the lack of cybersecurity (See Fig.4).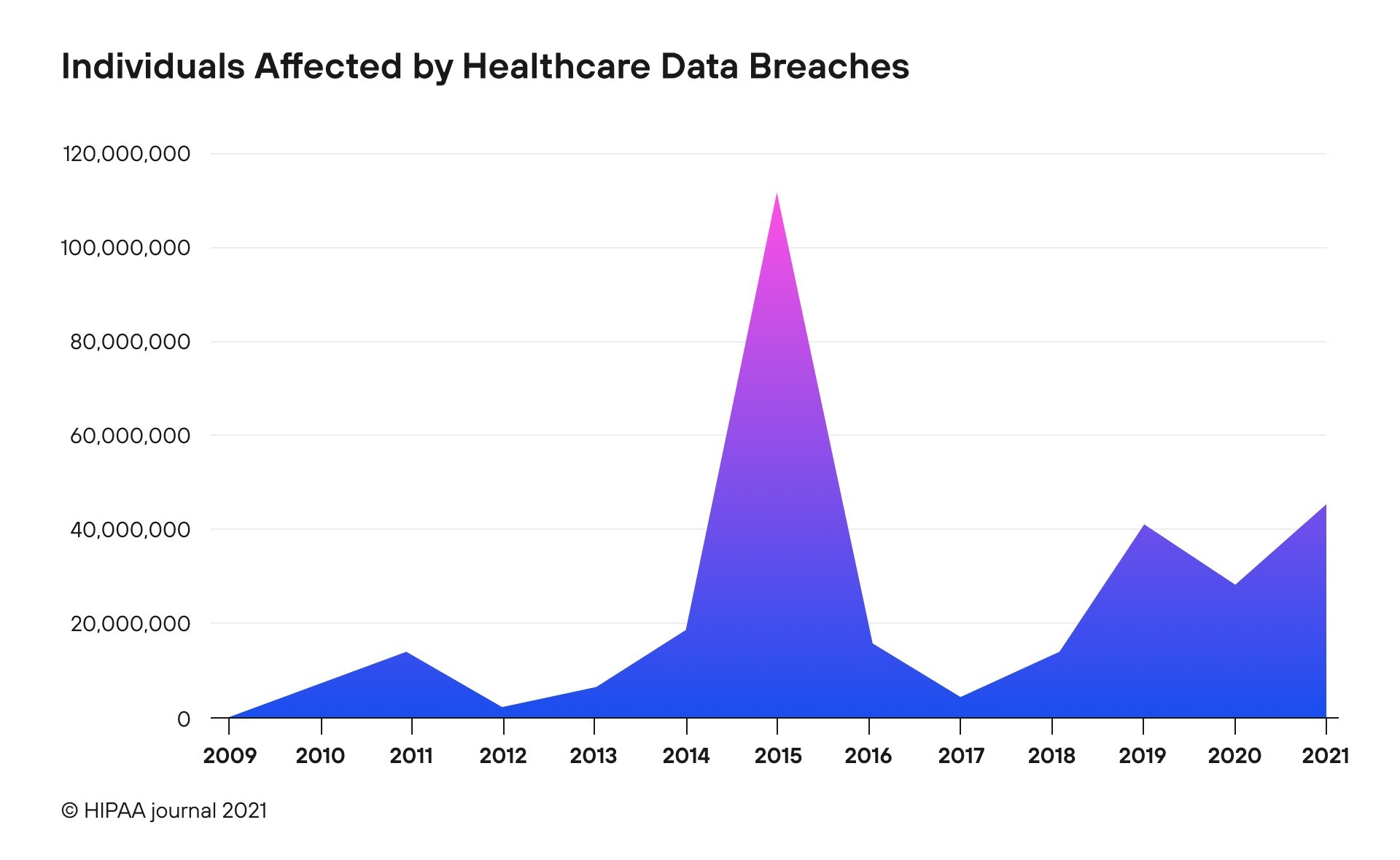 Figure 4. Individuals affected by healthcare data breaches.
Figure 4. Individuals affected by healthcare data breaches.
While GDPR noncompliance proved to be financially exhausting, compliance to the standard is fairly simple. Article 6 of the GDPR sets forth six foundational principles for processing personal data:
Following the aspects mentioned earlier ensures GDPR compliance. Keeping all the data security standards in mind and the consequences of noncompliance, it is worth noting several key elements currently helping to improve data protection in a respective industry.
Essentially, the experts outline nine steps for improving data protection in pharma. These include the following:
These simple steps do not take too much to complete. Yet, they ensure a healthcare provider or a pharmaceutical company has sufficient measures to protect patient privacy, avoid fines, and keep a competitive advantage.
Cybersecurity in pharma relies on anticipating risks and assessing the company’s ability to gather, properly store, and analyze sensitive data. To make the process easier, there are existing security standards. A pharmaceutical company does not need to invent the wheel all over again. It needs to do everything possible to comply with HIPAA, CCPA, and GDPR while also getting ISO 27001 and SOC 2 certification. These are the safeguards protecting pharma from reputational and financial damages that data breaches can inflict.
If you have any additional questions on HIPAA, CCPA, ISO 27001, SOC 2, and GDPR compliance, please contact us.
Ready to innovate your business?
We are! Let’s kick-off our journey to success!