Top Fintech trends 2025: The roadmap to smarter financial solutions
Embrace the top fintech trends 2025: from embedded finance to Amazonization, learn how financial service companies make smart decisions for a better future.

Cloud computing offers banks flexibility and saves costs. Yet, it also creates complex security and regulatory challenges.
Cybercriminals consider cloud platforms highly attractive targets, and attacks on financial services have risen by more than 20% in recent years. Additionally, the cloud computing banking market is booming and is expected to be worth five times more in 2032 compared to 2022. (see Fig. 1).
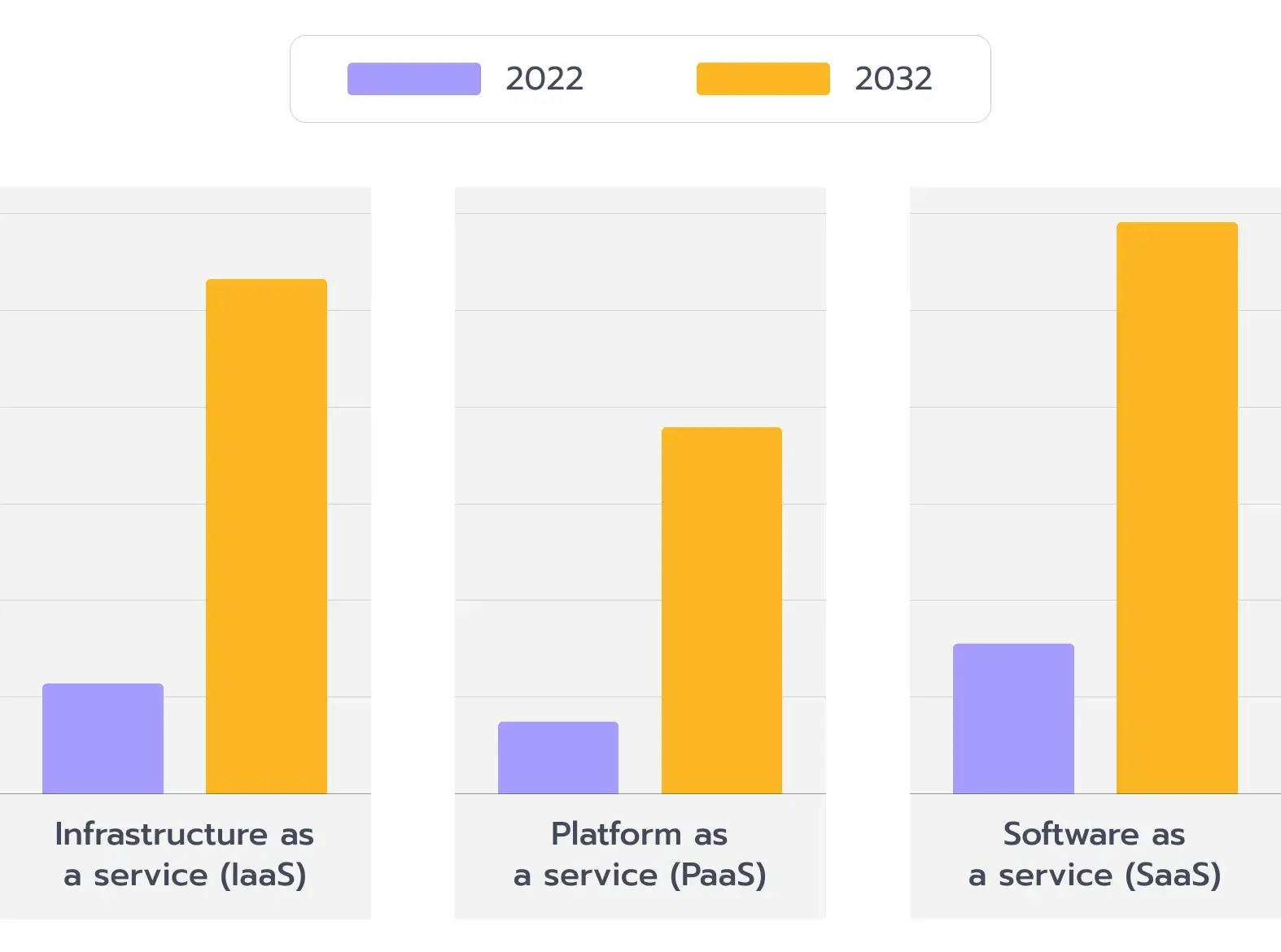
Figure 1. Cloud computing banking market by service
On top of the challenges brought by using cloud platforms and services, financial institutions must handle strict compliance rules while processing sensitive data and offering services. They must also keep up with changing regulations, such as the Digital Operational Resilience Act (DORA), which sets tighter standards for operational resilience in the EU. DORA came into force on January 16th, 2025. There is no time for financial institutions to stay aside and do nothing.
Insight 1: Banks cannot afford mistakes in cloud security.
A breach can cost millions, damage trust, and trigger hefty penalties. In the financial sector, the average cost of a data breach reached $5.97 million in 2022. Executives are feeling the pressure—knowing that regulators are closely monitoring and that clients expect robust security.
This article breaks down the complexity of cloud security in banking. It covers regulatory issues, common vulnerabilities, and strategies to improve protection. The goal is simple: help banks secure the cloud and meet strict requirements in regard to security and privacy.
Banks must follow many regulations. They must adhere to standards such as the Payment Card Industry Data Security Standard (PCI DSS), General Data Protection Regulation (GDPR), DORA, and local rules set by authorities.
Each set of rules contributes to a complex matrix of requirements. Compliance officers must balance various aspects such as data encryption, access controls, logging, and reporting. Since cloud vendors differ in their security controls, banks must carefully integrate these controls with their internal processes to ensure comprehensive security and compliance.
Insight 2: Banks must treat compliance as a continuous process.
Regulators expect continuous improvement and demand that banks consistently prove their ability to protect sensitive data. This often involves conducting frequent audits and penetration tests to ensure security measures are effective. It also means training staff to reduce human error and prevent insider threats, as well as tracking system changes in a Configuration Management Database (CMDB) to maintain consistency across environments.
To meet these stringent requirements, many banks opt for hybrid or multi-cloud setups. Sensitive data might be stored on-premises, while front-end services are run in the cloud. While hybrid models help satisfy regulatory demands, they also introduce additional complexity. Banks must ensure secure data flows and maintain compliance across every environment.
Failure to comply with these regulations can result in hefty fines. In Europe, regulators can impose penalties of up to 2% of global turnover for non-compliance with the Digital Operational Resilience Act (DORA). Similarly, U.S. regulators impose significant penalties. Banks need to understand the rules thoroughly and plan accordingly.
By meeting these compliance targets, banks minimize the risk of fines and data breaches, while also gaining the trust of both clients and regulators. A robust compliance strategy ensures the bank operates efficiently and securely in an increasingly cloud-dependent landscape.
Cloud adoption introduces new security threats. Cybercriminals are leveraging AI-driven malware and advanced phishing techniques to exploit misconfigurations and vulnerabilities in cloud environments. Their primary goal is to gain access to accounts, sensitive data, and payment systems. The risks intensify when dealing with sensitive payment card information or personal client details. Attackers are constantly searching for weak links in security defenses.
Financial institutions must focus on these critical risks:
Insight 3: Banks and other financial entities must invest in cloud visibility and monitoring.
Financial institutions can prevent costly data breaches by knowing the threats and taking the right steps. This way, they can offer services safely and keep trust.
A clear roadmap for cloud security is a lifeline for financial entities. It means navigating different frameworks. Keep in mind both technical and organizational elements are important.
Here are some essential steps to consider.
Financial entities should begin by aligning their cloud systems with standards like ISO 27001 and SOC 2. The aforementioned certifications are needed to reduce the risk of data breaches and help manage incidents effectively.
Encrypting data at rest and in transit is a must. Frequent key rotation and using a Key Management Service (KMS) help keep encryption keys safe from attackers.
Banks must use Multi-Factor Authentication (MFA) for all critical accounts. Limiting user privileges also lowers the chance of internal threats.
Timely patching, secure images, and network segmentation are essential for defending against attackers. Banks must regularly assess their security posture, monitor progress, and perform frequent testing. This continuous feedback loop enables them to adapt to emerging threats and ensures compliance with regulatory standards.
Additionally, effective security monitoring and incident response are key elements in maintaining security. By actively tracking emerging threats and addressing incidents promptly, banks can mitigate potential damage and maintain compliance.
By implementing these practices, banks not only meet compliance requirements but also safeguard their assets. They are able to detect and address issues early, respond swiftly to incidents, and stay aligned with evolving regulations and threats.
Cyber threats are constantly evolving, and banks cannot afford to adopt a “set it and forget it” approach to security. Continuous improvement of controls and regular testing are essential. Penetration testing and red teaming help identify blind spots, while dynamic application security testing (DAST) and static application security testing (SAST) focus on uncovering code-level vulnerabilities. These tests validate and strengthen the bank’s security posture.
In addition, darknet monitoring and threat hunting provide an additional layer of precaution. These proactive measures help detect and address potential incidents before they occur or prevent known vulnerabilities from being exploited.
Key activities to support continuous improvement
1. Testing defenses:
2. Monitoring activities:
3. Third-party oversight:
Banks must handle complex security requirements while meeting strict standards. Experts at Avenga have worked with finance industry clients for many years and understand these needs.
Avenga can assist financial institutions throughout the entire journey. The key goal is to help you stay compliant, protect your data, and uphold client trust.
Banks and other financial institutions grapple with tough cloud security demands. They must follow strict rules and combat advanced threats to maintain client trust.
The right mix of technology, training, and oversight helps stay ahead of threats and meet regulatory demands.
Ready to strengthen your cloud security strategy? Contact our team of experts today. Let’s discuss how to protect your data, meet regulations, and maintain trust in the cloud.
Ready to innovate your business?
We are! Let’s kick-off our journey to success!