3. Control. Audit capability refers to one of the integral features of Key Vault. It empowers companies to seamlessly supervise access to their applications, thus they benefit from complete transparency and control. With Key Vault, you can monitor all user activities and choose to archive logs to a storage account, stream them to an event hub for real-time supervision, or send them directly to Azure Monitor logs for centralized secrets management and analysis. Besides, logs can have restricted access or be deleted whenever they become irrelevant. This feature lets users adopt a logging and auditing approach that aligns with their specific objectives and compliance requirements.
4. Simplicity. With the growing complexity of data storage techniques, organizations typically strive to deploy well-orchestrated services that streamline the management of sensitive information and help ensure that security measures are seamlessly incorporated into their applications. Key Vault lends itself to these challenges. Firstly, there is no need for in-house knowledge of Hardware Security Modules if your team leverages this solution. Secondly, it makes it possible to replicate the same security configuration across all applications. You can avoid creating custom code and ultimately reduce the potential for human error. Consequently, by automating numerous tasks involved in secret management, such as key rotation and certificate renewal, this tool reduces manual intervention and lowers the risk of data breaches.
5. Interconnectedness. As a powerful element of the ecosystem, Key Vault easily integrates with multiple Azure services. It can protect and manage secrets and keys across multiple applications, particularly Azure Logic Apps, Azure Virtual Machines, or Azure Data Factory. These integration options open up room for a convenient migration to Azure and at the same time deliver a comprehensive suite of services for the company’s specific needs. In addition to being seamlessly aligned with other Azure services, Key Vault also offers integration with third-party solutions, such as Kubernetes. This powerful range of possibilities results in a more comprehensive and flexible approach to secure key management across different platforms and environments.
Given these advantages, Azure Key Vault serves as a valuable and convenient tool for businesses striving to safeguard their security posture, protect data, and beef up their use of the Azure ecosystem. Moreover, it continues to evolve and expand its features so as to guarantee that businesses can stay ahead of emerging threats and stay competitive along the way.
Azure Key Vault: Use cases
As we previously discussed, companies can deploy Azure Key Vault into various scenarios where they need to manage securely stored credentials and protect their cryptographic keys, secrets, and certificates within chosen applications. Let’s take a closer look at several use cases that will show the versatility of Key Vault in addressing different technical tasks.
1. Incorporation of cloud-based data into on-premises data storage with Logic Apps and SQL Server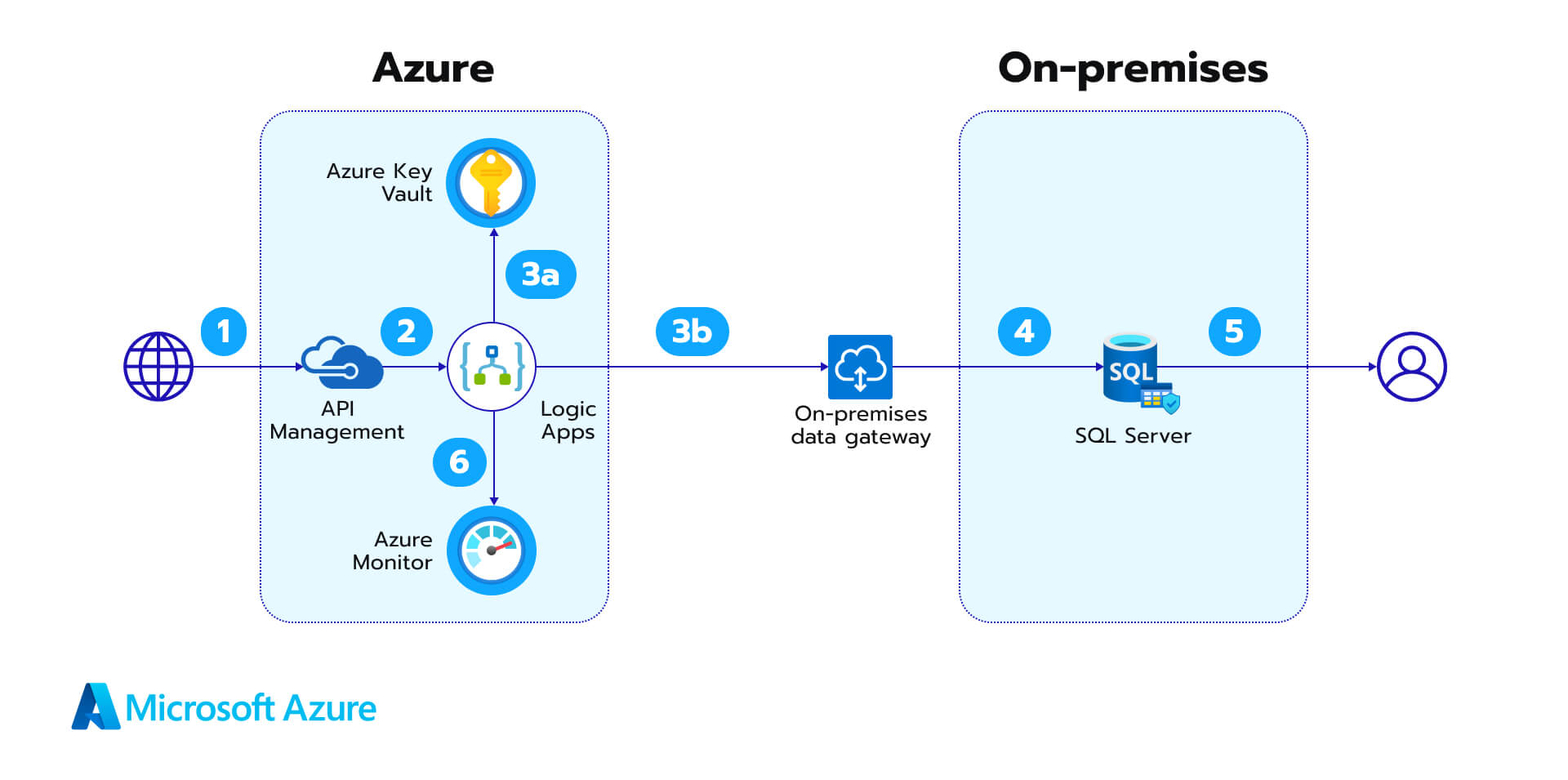
Image courtesy of Microsoft
You can deploy this framework to streamline data integration procedures, though it weighs heavily on the following elements: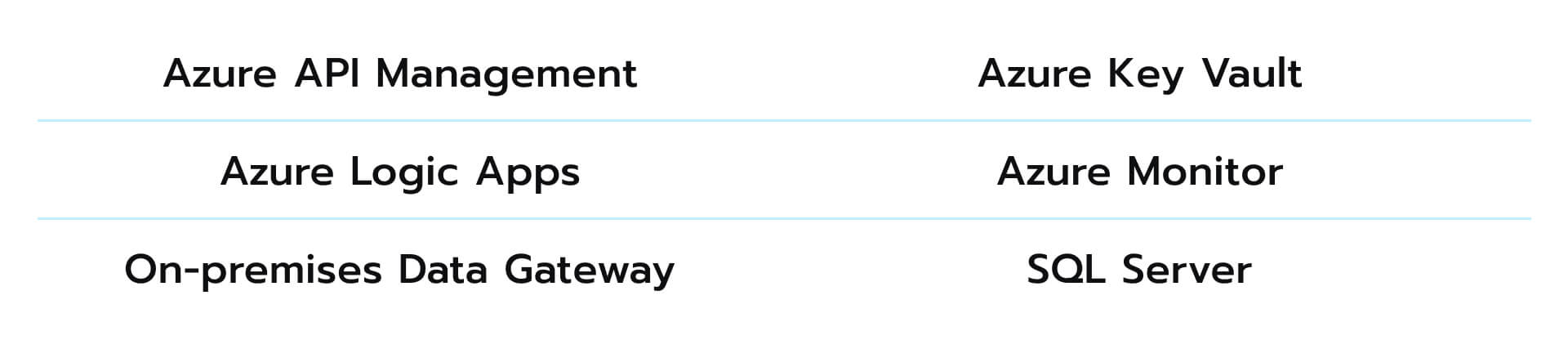 In this workflow, API calls are processed by an API Management solution (1) and then transferred to Logic Apps (2) as HTTP requests. The integration of Azure API Management further enhances security when it comes to the verification of keys, tokens, certificates, and other credentials before routing API calls to Logic Apps. In the next step, every HTTP request causes a set of actions within the Logic Apps (2), where Key Vault (3a) serves as a source of database credentials which enables proper authentication and smooth data protection (4). With Key Vault, this architecture prioritizes the confidentiality and integrity of data integration processes.
In this workflow, API calls are processed by an API Management solution (1) and then transferred to Logic Apps (2) as HTTP requests. The integration of Azure API Management further enhances security when it comes to the verification of keys, tokens, certificates, and other credentials before routing API calls to Logic Apps. In the next step, every HTTP request causes a set of actions within the Logic Apps (2), where Key Vault (3a) serves as a source of database credentials which enables proper authentication and smooth data protection (4). With Key Vault, this architecture prioritizes the confidentiality and integrity of data integration processes.
2. Azure healthcare blueprint for Artificial Intelligence (AI)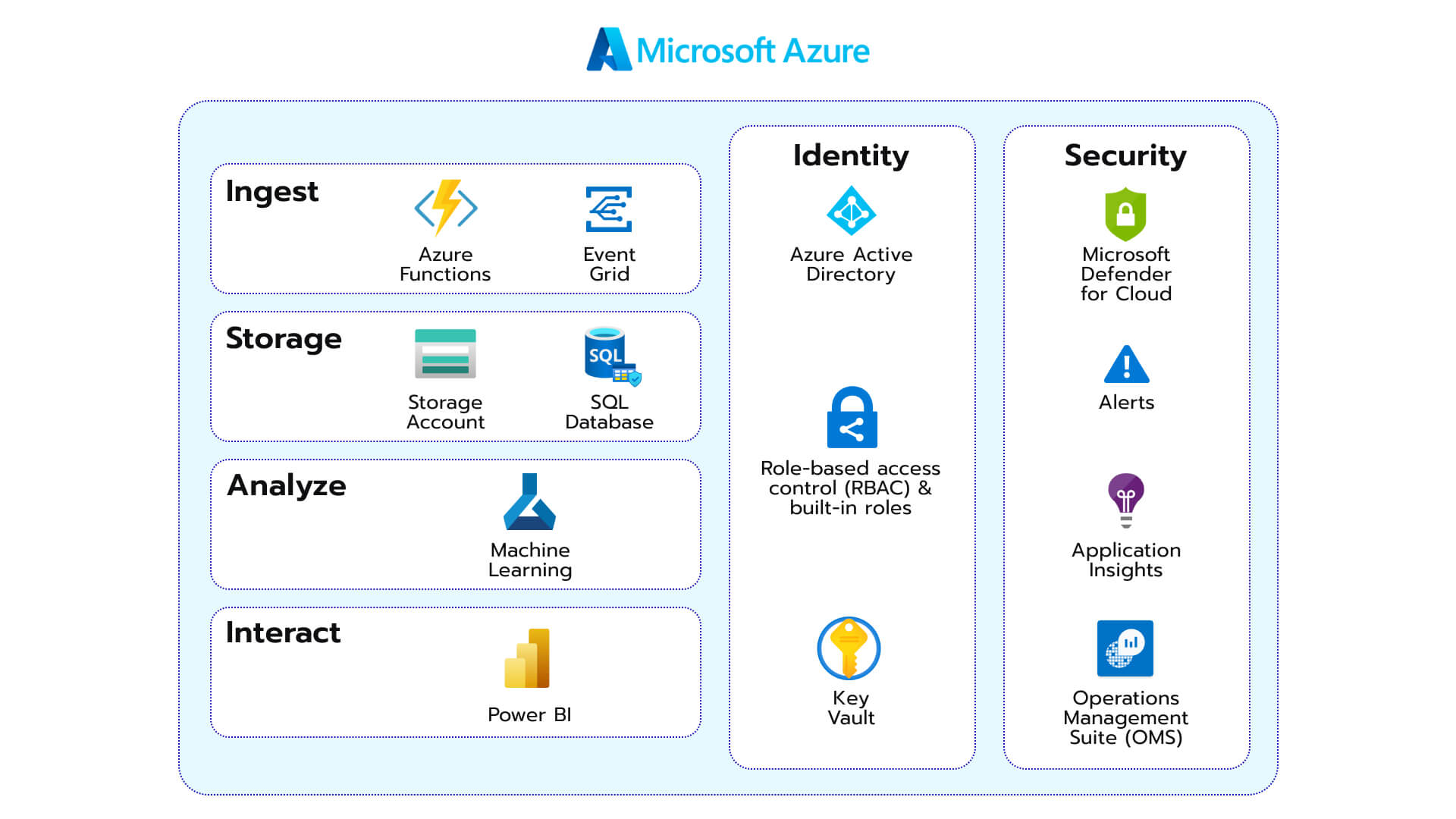
Image courtesy of Microsoft
Healthcare organizations continue to adjust to the constantly evolving landscape, by transfusing their daily operations with AI and Machine Learning (ML). This guideline showcases how to integrate Azure services for enhanced use of these rapidly advancing technologies in a secure and compliant manner. In the listing below, you can learn how to set up proper PaaS (Platform as a Service) architectures. These are the integral elements of the blueprint: In this architecture, Key Vault provides a reliable and compliant solution for storing and managing the sensitive data used by applications. From database strings to REST endpoint URLs and API keys, it can securely store the credentials for accessing data sources and stay responsible for the encryption keys used to protect sensitive patient data. Additionally, Key Vault monitors key usage in order to detect any potential security issues.
In this architecture, Key Vault provides a reliable and compliant solution for storing and managing the sensitive data used by applications. From database strings to REST endpoint URLs and API keys, it can securely store the credentials for accessing data sources and stay responsible for the encryption keys used to protect sensitive patient data. Additionally, Key Vault monitors key usage in order to detect any potential security issues.
3. Robust OAuth 2.0 On-Behalf-Of (OBO) token refresh mechanism for web services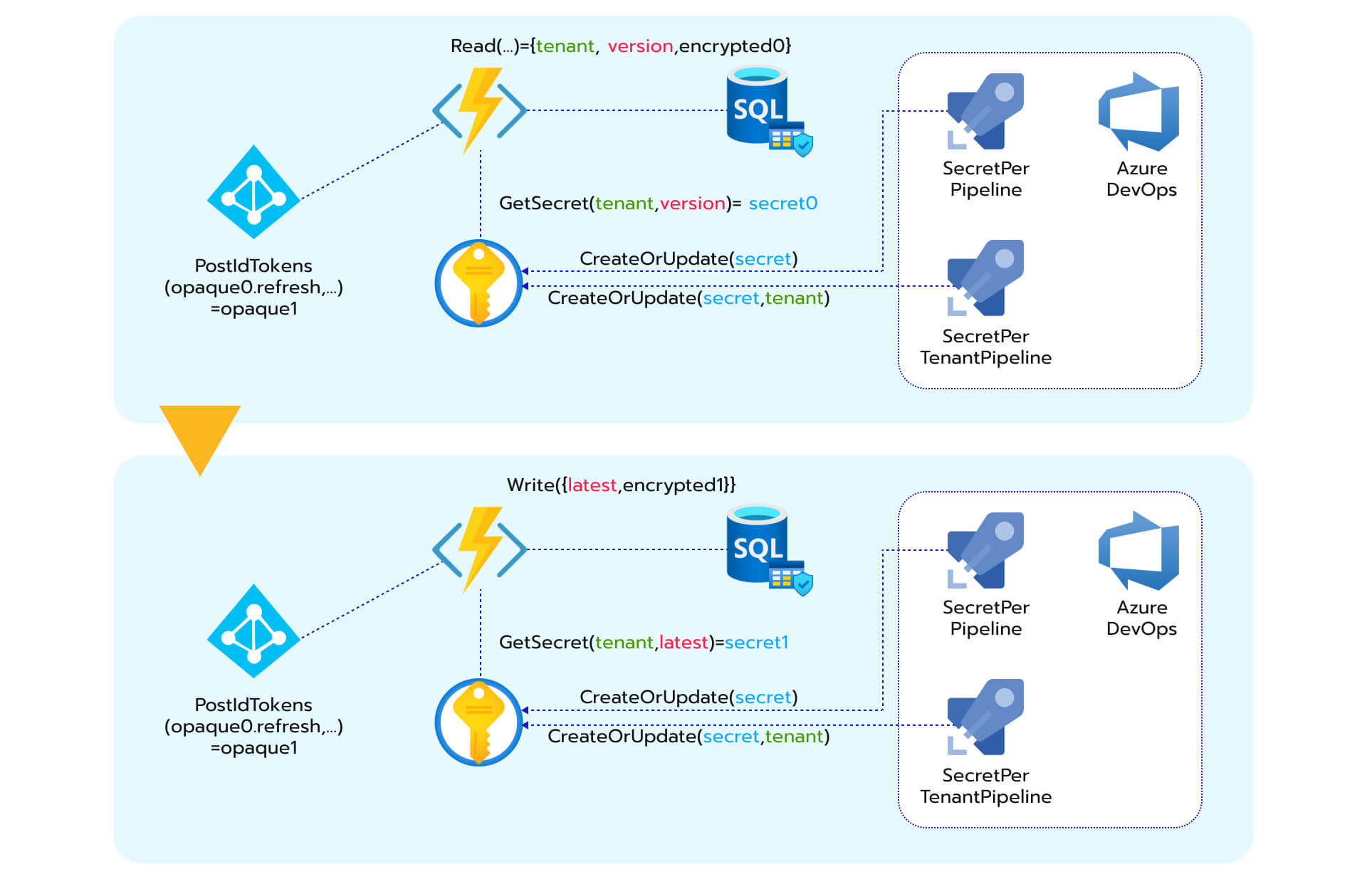
Image courtesy of Microsoft
Here are the resources that are necessary for this workflow: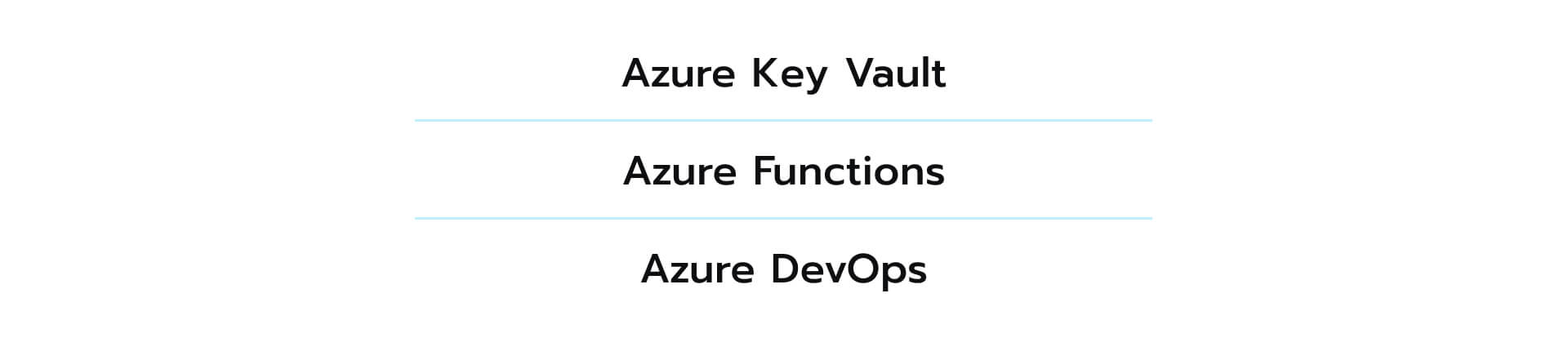 This blueprint leverages Azure Key Vault’s secure storage capabilities, Azure Functions for periodic key retrieval and token storage, a database for storing encrypted keys, and Azure DevOps for managing the secret rotation and token refresh processes. In combination, these instruments enable a secure and efficient mechanism for managing OAuth 2.0 OBO refresh tokens in web service development. They propel the longevity and security of access and refresh tokens, particularly in situations associated with offline access, and adhere to top-notch practices for secure key storage and access management.
This blueprint leverages Azure Key Vault’s secure storage capabilities, Azure Functions for periodic key retrieval and token storage, a database for storing encrypted keys, and Azure DevOps for managing the secret rotation and token refresh processes. In combination, these instruments enable a secure and efficient mechanism for managing OAuth 2.0 OBO refresh tokens in web service development. They propel the longevity and security of access and refresh tokens, particularly in situations associated with offline access, and adhere to top-notch practices for secure key storage and access management.
In this scenario, Key Vault acts as a centralized repository for secret encryption keys that are specific to each Azure AD tenant. The solution allows us to maintain the confidentiality of refresh tokens and securely store them alongside the latest secret key version. Additionally, the integration of Azure Functions streamlines the periodic retrieval of the latest secret key from Key Vault and the retrieval of refresh tokens from the Microsoft identity platform.
Final thoughts
Azure Key Vault is a highly useful resource that assists organizations in meeting their security and compliance requirements, and confidently protects sensitive data. Its centralized, secure, and scalable architecture makes it possible for businesses to effectively monitor access to essential information and minimize the risk of data breaches. In addition, its integration with other Azure services, such as Virtual Machines, Logic Apps, or Data Factory, further enhances its functionality and usability. Given these advantages, Key Vault simplifies the process of managing cryptographic keys and secrets, reduces the need for further in-house expertise, and serves as a multi-facet solution for companies of all sizes.
Avenga is an international tech company with deep industry knowledge in pharma, insurance, finance, and automotive. The company’s IT specialists operate from 8 countries around the world and support digital transformation with projects along the entire digital value chain – from digital strategy to the implementation of software, user experience, and IT solutions, including hosting and operations. Interested in building a transparent and productive technology partnership? Contact us.



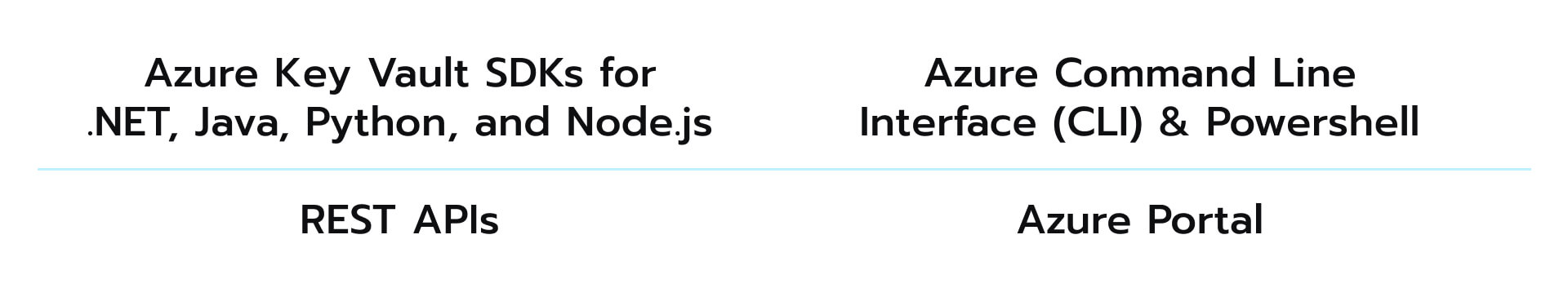 These access methods allow for greater flexibility and ease of integration into the various development environments of Key Vault. The REST APIs, for example, are suitable for use in any programming language. This characteristic opens up room for developers with different technical backgrounds when it comes to seamlessly aligning the solution with the company’s goals. At the same time, the Azure SDKs (software development kits) offer direct access to a more streamlined and intuitive experience for specialists working within the Azure ecosystem.
These access methods allow for greater flexibility and ease of integration into the various development environments of Key Vault. The REST APIs, for example, are suitable for use in any programming language. This characteristic opens up room for developers with different technical backgrounds when it comes to seamlessly aligning the solution with the company’s goals. At the same time, the Azure SDKs (software development kits) offer direct access to a more streamlined and intuitive experience for specialists working within the Azure ecosystem.
 In this workflow, API calls are processed by an API Management solution (1) and then transferred to Logic Apps (2) as HTTP requests. The integration of Azure API Management further enhances security when it comes to the verification of keys, tokens, certificates, and other credentials before routing API calls to Logic Apps. In the next step, every HTTP request causes a set of actions within the Logic Apps (2), where Key Vault (3a) serves as a source of database credentials which enables proper authentication and smooth data protection (4). With Key Vault, this architecture prioritizes the confidentiality and integrity of data integration processes.
In this workflow, API calls are processed by an API Management solution (1) and then transferred to Logic Apps (2) as HTTP requests. The integration of Azure API Management further enhances security when it comes to the verification of keys, tokens, certificates, and other credentials before routing API calls to Logic Apps. In the next step, every HTTP request causes a set of actions within the Logic Apps (2), where Key Vault (3a) serves as a source of database credentials which enables proper authentication and smooth data protection (4). With Key Vault, this architecture prioritizes the confidentiality and integrity of data integration processes.
 In this architecture, Key Vault provides a reliable and compliant solution for storing and managing the sensitive data used by applications. From database strings to REST endpoint URLs and API keys, it can securely store the credentials for accessing data sources and stay responsible for the encryption keys used to protect sensitive
In this architecture, Key Vault provides a reliable and compliant solution for storing and managing the sensitive data used by applications. From database strings to REST endpoint URLs and API keys, it can securely store the credentials for accessing data sources and stay responsible for the encryption keys used to protect sensitive 
 This blueprint leverages Azure Key Vault’s secure storage capabilities, Azure Functions for periodic key retrieval and token storage, a database for storing encrypted keys, and Azure DevOps for managing the secret rotation and token refresh processes. In combination, these instruments enable a secure and efficient mechanism for managing OAuth 2.0 OBO refresh tokens in web service development. They propel the longevity and security of access and refresh tokens, particularly in situations associated with offline access, and adhere to top-notch practices for secure key storage and access management.
This blueprint leverages Azure Key Vault’s secure storage capabilities, Azure Functions for periodic key retrieval and token storage, a database for storing encrypted keys, and Azure DevOps for managing the secret rotation and token refresh processes. In combination, these instruments enable a secure and efficient mechanism for managing OAuth 2.0 OBO refresh tokens in web service development. They propel the longevity and security of access and refresh tokens, particularly in situations associated with offline access, and adhere to top-notch practices for secure key storage and access management.






